What is a Distributed Denial-of-Service attack?
A denial-of-service attack, as the name implies, is an attempt by the attackers. This is to prevent users from accessing a networked system, service, website, application or other resource. The attack typically makes a system slow to react, or it can completely disable the system.
An attack originating from a single source is simply call a denial-of-service (DoS) attack. Far more common today, however, are distributed denial-of-service (DDoS) attacks, launch from multiple sources at a target but orchestrate from a central point. Distribute attacks are larger, potentially more devastating and sometimes harder to detect and stop for the victim.
Whether DoS or DDoS, the result is the same legitimate users will be unable. This is to connect to the resources to which they intend to access. Next, DDoS attacks are one of the most effective ways for malicious actors to breach availability, the third of three basic principles of security— confidentiality, integrity, and availability— in what is call the CIA triad.
How Does a DDoS Attack Work?
Many DDoS attacks are design to absorb all available bandwidth or resources on a target network, device, or website. The attacker uses one of many methods and tools available to flood the target with a barrage of malicious or nuisance requests, or to abuse a protocol or inherent vulnerability to prevent the system from responding to requests. The effects of a DDoS attack are a bit like having the entrance to a concert venue swarming suddenly with busloads of troublemakers with fake tickets. The legit holders of tickets, standing in an orderly line, would never get inside.
The role of Botnets in DDoS Attacks
From a single computer, the volume of traffic need to crash a network or website is difficult for the attackers to generate. To get the bandwidth or processing power need. Next, attackers often use botnets armies of hundreds or thousands of Internet-connecte computers (zombies or bots). That are malware-infect and under attacker control (the bot master, or bot herder). In most cases, the owners of these infect computers are not even aware they’ve been compromise.
From one or more computers designated as the command and control (C&C) server, the attacker sends remote “launch” instructions to the bots. Collectively, these systems provide enough power to carry out massive attacks—far larger than those launched from a single source. And by using a botnet, attackers are able to hide their identity because the attack originates from many different systems that all appear to be legitimate.
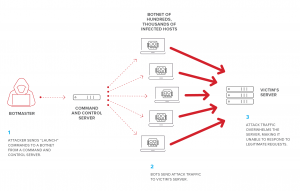
In the beginning, attackers built their own botnets by scanning the Internet for vulnerable devices. Then compromising them with malware that enabled attackers to remotely control the bots. Sadly, attackers don’t even need to build botnets anymore; they can rent DDoS-for-hire botnets from operators who charge very little money for short-term (but effective) attacks.
While a fair number of botnets are still made up of infect PCs, increasingly. Today’s botnets consist of compromise Internet of Things (IoT) devices. As the number of these devices (from home appliances and toys to fitness devices and sleep aids) grows into the multi-billions. Next, the problem of malicious bots being used by attackers is skyrocketing. Many IoT devices are perfect zombie candidates because they’re build without any security protections (for example, the same default password is use across thousands of devices). By making them extremely easy for attackers to exploit.
Who is a Target of DDoS Attacks?
Regardless of size or industry, virtually any organization having a website that is open to the public is vulnerable to DDoS attacks. Public-facing websites are design by their very nature to invite visitors in. Which inherently makes them a potential target for attackers. Unmonitore and poorly protecte networks are particularly vulnerable. As there are no security mechanisms in place to alert administrators to intrusions, anomalous behaviour or traffic volume fluctuations.
But who is going to get target? While all businesses are warned to plan for “when, if not” some are more likely targets than others. With simply because of their business nature. F5’s own attack data indicates that in 55 per cent of the DDoS attacks investigated in 2018, financial services and web hosting and colocation facilities were targets.
DDoS attacks are often just one step in a multi-level attack in the case of financial services. Also, usually use as a diversion for a larger assault aimed at stealing account information or taking over accounts. In the case of web hosting companies and colocation facilities their own customers end up being collateral damage in such attacks. Although not directly targeted. Other obvious targets are retail and ecommerce websites whose revenue depends heavily on the availability and responsiveness of their websites.



