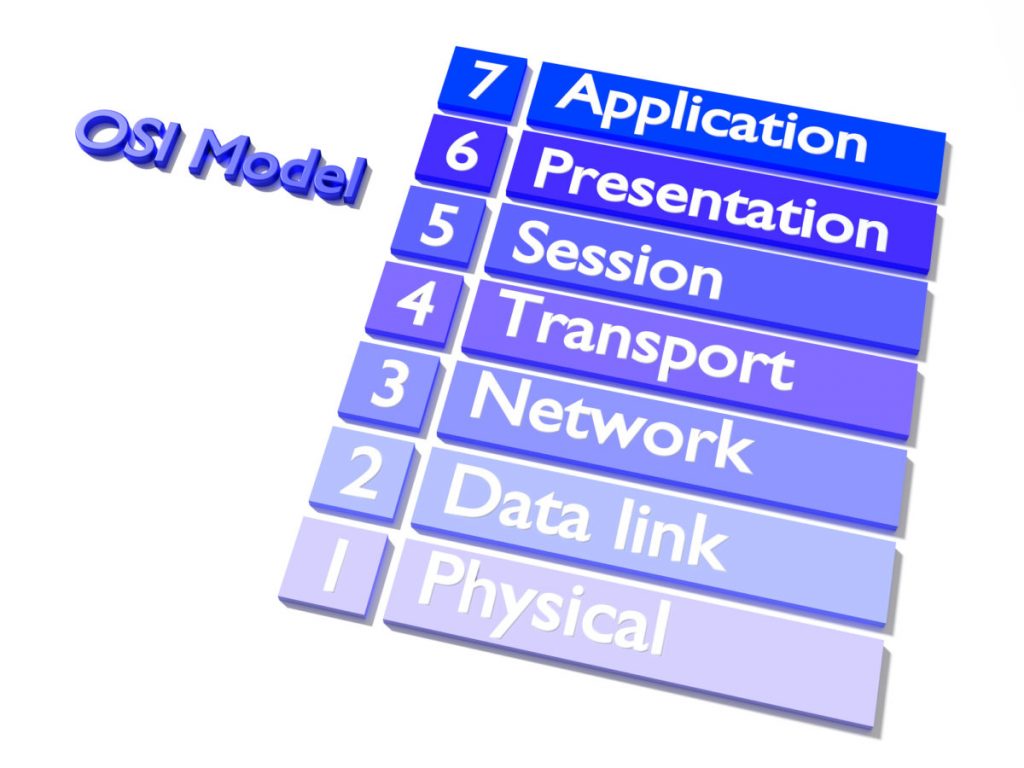
How to remove malware manually
When a website owner is tell that their site has been infect with malware. It can come as quite a shock. After the shock wears off, and knowing the immediate impact. While, it’s important to take stock of what really happened behind the scenes and then clean it up. The best advice that anyone can …